Industrial Firewall DMZ(IDMZ)
An Industrial Demilitarised Zone (IDMZ) firewall is a specialised security boundary that acts as a buffer between an industrial control system (ICS) network and an enterprise IT network.

I’ve just completed a design for an Industrial DMZ firewall for a train transport company. They used a Cisco Firewall Threat Defence (FTD), which acts as a layer of protection between their corporate IT systems and their operational train systems, such as High-Capacity Systems (HCS) and critical train control systems.
IDMZ Overview
Below is a brief overview of the IDMZ firewall's function and the IDMZ zone.
The IDMZ is a critical layer of protection between the enterprise zone and Operational Technology (OT) systems. It also allows for a location where protected services can be provisioned if required. The IDMZ is a concept derived from the International Society of Automation (ISA) standard ISA99 and further developed in collaboration with the International Electrotechnical Commission (IEC) to create common security standards, as outlined in ISA/IEC 62443.
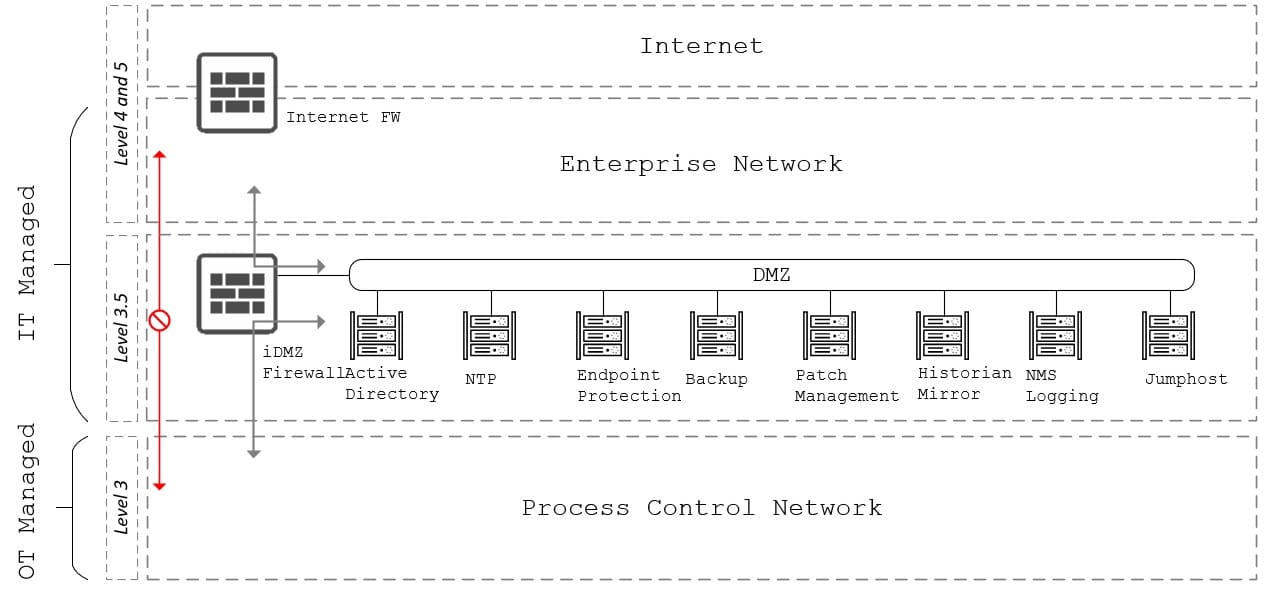
The IDMZ firewall is located within level 3.5 of the Purdue model and should be regarded as an IT-managed and owned system. It serves as a vital layer of defence for the Process Control Network (PCN) and OT environments. There should be no direct communication between the PCN and levels 4 and 5 (Enterprise and Internet), as these zones are considered the least secure and are primary sources of security threats. Some vendor products provide a web proxy service for patch management (FortiGate, Palo). Additionally, dedicated patch management services can be implemented in DMZs that sit outside the IDMZ firewall. Direct traffic flows from Level 3 to Level 4 and 5 should NOT be allowed.
The following points define the three (3) key areas for the IDMZ firewall:
- The enterprise zone: The area where all IT-controlled environments reside, such as corporate data centres, LAN, WAN, and business applications. Within the IEC standards, this is deemed untrusted.
- The Industrial Demilitarised Zone (IDMZ): The buffer between critical environments and the enterprise network. All shared services across environments should reside in this environment. The DMZs within this zone can contain jump servers, patch management servers, antivirus servers, and servers for monitoring and logging.
- The industrial security zone: This zone is the location for critical operations for Industrial Control Systems (ICS), which can be referred to as the Process Control Network
Below is a high-level design overview of the concept:
I would consider a vendor product that has the capability of a web proxy function, without compromising industrial cybersecurity design philosophies. This will enable access for patch management, software updates, and other related tasks.
I find the topic of industrial cybersecurity quite interesting; hopefully, I will have the opportunity to work on more in-depth OT design projects in the future, allowing me to write about the topic further.




