The Physical Stakes: The New Importance of Protecting ICS Systems

If you work in manufacturing, energy, utilities, or critical infrastructure, the stakes of your cybersecurity are profoundly different. You are not just guarding data—you are guarding things that spin, pump, flow, and explode. The key focus is to protect the process, rather than the information itself.
This is the world of Industrial Control Systems (ICS) and Operational Technology (OT). While traditional Information Technology (IT) prioritises confidentiality, the OT environment focuses on availability and safety.
The CIA (Confidentiality, Integrity, and Availability) triad was a standard methodology for protecting data in information systems. However, with OT systems, the focus is on the integrity and availability of the system itself, with this triad rotated to AIC. (Availability, Integrity and Confidentiality) with an emphasis on the stability and availability of the system itself, with a safety-first view. This is shown in the diagram below:
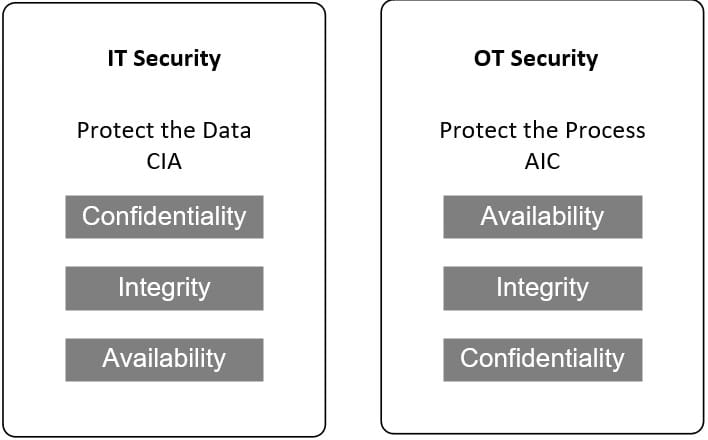
The disruption of a process or the failure of Safety Instrumented Systems (SIS) could lead to significant financial loss, ecological catastrophe, and loss of life.
OT’s common security focus in the past was to “Air Gap” their solution and network, with security achieved through obscurity, removal of access and process. However, as the corporate IT network has merged with the OT network (I.T/Convergence) and the greater digitisation of OT systems has occurred, OT designers must rethink the way they view their networks and systems, as their networks are now exposed to greater threats. The main path into OT networks via IT networks can be protected via the IDMZ.
The attack that changed everything. Stuxnet was considered the first of its kind and was regarded as a form of cyber warfare, funded by a state actor(s) against Iran’s nuclear program, destroying multiple nuclear reactors, and setting back their nuclear program for numerous years. Multiple ICS attacks have been carried out since 2010; examples are provided below.
ICS Case Studies
Stuxnet (2010)
Stuxnet is a sophisticated computer worm designed to target Iran's nuclear enrichment facilities by sabotaging programmable logic controllers (PLCs), causing physical damage to centrifuges while hiding its activity from operators.
Flame (2012)
Flame is a large-scale cyber-espionage malware discovered in 2012, targeting Middle Eastern organisations for data theft and surveillance, with capabilities including keystroke logging, screenshot capture, and audio recording.
Havex (2013)
Havex is a Remote Access Trojan (RAT) deployed by the Dragonfly/Energetic Bear group, primarily targeting ICS through supply chain attacks. It mapped industrial networks using OPC scanning and facilitated espionage rather than direct sabotage.
Black Energy (2015)
Black Energy is a versatile malware toolkit, initially used for distributed denial-of-service (DDoS) attacks but later adapted to target ICS and SCADA systems. Its notable usage includes cyber-attacks against Ukrainian power infrastructure, facilitating disruption and espionage activities.
This document here was a comprehensive review of the incident.
Industroyer / Crashoverride (2016)
Industroyer, also known as CrashOverride, is malware specifically designed to target electrical grids. Notably used in the 2016 Kyiv power grid attack, it exploited industrial protocols to directly manipulate substation equipment, demonstrating the capacity for large-scale power outages.
Trisis / Triton (2017)
Trisis, also known as Triton or Hatman, is a specialised malware that targets safety instrumented systems (SIS) in industrial settings, especially Schneider Electric’s Triconex controllers, with the intention of disabling safety systems and increasing the risk of physical damage and danger.
Summary
Many attacks can disrupt the process and cause a system crash. This might prevent the sensor from communicating with the controller (PLC, etc.). Such attacks can be efficiently conducted using tools like Kali Linux by manipulating the Modbus packets to make the device appear as though the sensor readings are regular.
The examples provided above were carried out and funded by state actors and would be a challenge to protect against; however, they can be achieved with new ways of thinking, additional levels of process to protect vulnerable systems, such as engineering workstations that access PLCs, and sufficient segmentation. The following diagram describes the methods to safeguard OT and ICS systems:
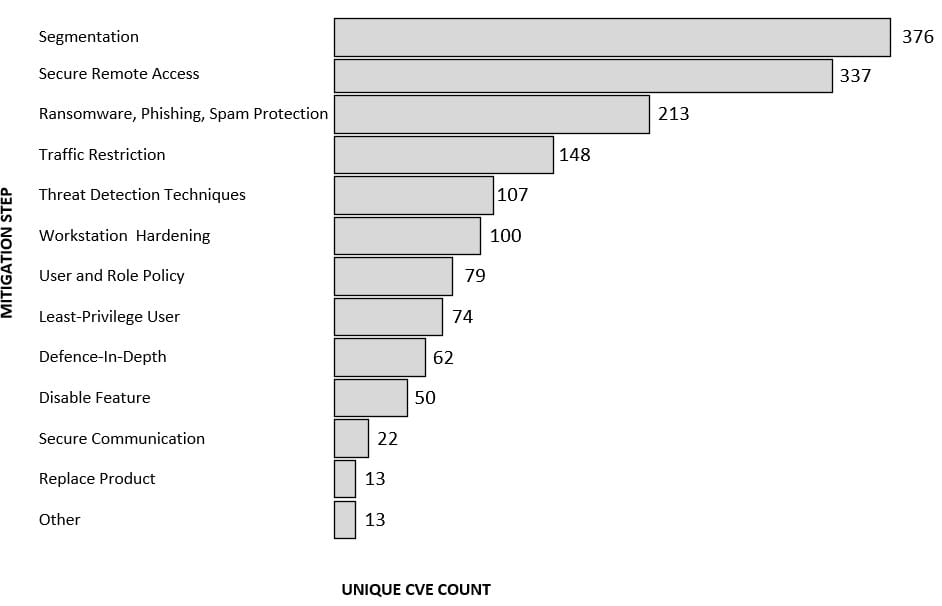
I will discuss methods for protecting and hardening OT and ICS networks and systems in a future post.




